Google published a 2016 #NoHacked year in review Monday on its Webmaster Central Blog. Its chief finding is that the number of websites suffering attacks increased by 32 percent from 2015 to 2016.
Google started #NoHacked as a weeklong social campaign in August 2014 and has continued the work with posts and advice during the summer of 2015 and throughout the winter holiday season in 2016.
The good news? Google noticed an 180 percent increase in the number of websites being hacked between 2014 and 2015. In that context, a 32 percent increase is an improvement. The bad news? Hackers are unlikely to give up. Google expects groups to continue to forcefully target websites of all sizes using a variety of methods of attack.
According to Google, SEO spam is one of the primary reasons vulnerable websites are targeted. SEO spam includes practices like redirecting users, link injection and content injection — all intended to artificially boost the attackers' sites and take value from yours. According to web security company Sucuri, SEO-related infections accounted for 31 percent of all attacks in 2016, up from 20 percent in 2014.
What do hackers want with a law firm website, anyway?
It is easy to assume that hackers only target websites of large, national brands. That is not the case. Hackers will target a site of any size, because these sites offer value in several ways.
Access to your servers: In many cases, hackers want your server resources. Once they have access to your servers, they can hijack them and use them to launch further attacks.
Access to your visitors: Hackers may want to use pages on your site to infect the devices of people who visit them. Once they infect your visitors' computers, they can retrieve sensitive information from the source.
Access to your traffic: Some hacks involve injecting cloaked links or content in an attempt to gain an SEO boost. Others will cause a visitor to be redirected to a page on another server, usually a porn site, when he or she clicks on what looks like a link to one of your pages.
What can you do?
1. Use secure passwords
Compromised passwords are one of the main avenues hackers use to gain access to vulnerable websites. Sometimes it is easy for a hacker to guess a password; he or she must simply look at publicly available data, like family surnames, pet names, birthdays or alma maters. Others use malware that installs a tool to collect data, like a keystroke logger, or a threat, like ransomeware.
However, many passwords are uncovered through brute force attacks, in which software is used to guess every possible combination of characters until it hits a password that works. Brute force attacks are very effective against short passwords and passwords without a lot of variation in characters. For example, it will take a brute force bot approximately 14 hours to hack a password that is eight characters long and uses a combination of uppercase and lowercase letters but only 208 seconds to hack an eight character password that uses only lowercase letters.
Up the complexity, and the time it will take to crack the password increases exponentially. An eight character password that uses a combination of all letters, numbers and symbols will take 70 days to crack, and a 12 character password of the same complexity would take 15,091,334 years.
When creating passwords, never use common words or personal information. Try to create passwords that are at least 8 characters long — preferably 12 or more — and that use a combination of upper and lower case letters, numbers and special characters.
Additionally, set up 2-factor authentication on your website logins, which requires you to use a password as well as a piece of data to which only you could have access, like a code sent to a phone or email address. Finally, don't use the same password over multiple websites.
2. Keep your servers, content management system and plugins updated
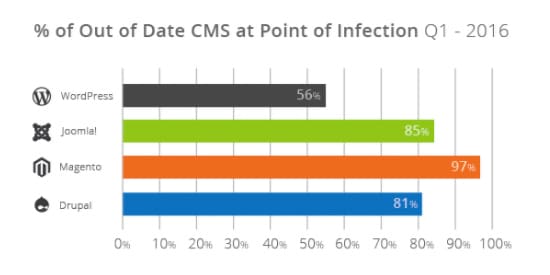
Hackers are constantly looking to uncover and exploit vulnerabilities in popular content management systems, particularly WordPress, and in any associated plugins. Every time a weakness is exposed, responsible developers will release a software update that patches the hole. In 2016, WordPress released 26 official updates, and the organization has released three security-specific updates since January 2017. Keeping up-to-date with CMS releases will help protect your website from known vulnerabilities. According to Securi, in the first quarter of 2016, 56 percent of WordPress websites, 85 percent of Joomla websites and 91 percent of Magento websites were out-of-date when an infection occurred.
Plugin developers must also be vigilant in checking for and patching security holes in plugin releases. For this reason, you should only use plugins on your site that are supported and updated regularly.
Your hosting company should also perform regular updates to its web server software, particularly after any potential issue with the software has been exposed. Check with your hosting company about its security update and server maintenance policies and history.
3. Avoid free themes
It may be tempting to use a free theme to set up your website. Free themes have their own issues in terms of branding and uniqueness. Marketing aside, however, free or unsupported themes may have serious security troubles. If you purchase a theme, always keep it updated. If you have invested in a custom theme, check with your marketing team to be sure it is routinely checked for vulnerabilities and patched if necessary.
4. Be on the lookout for social engineering
A social engineering attack relies on human behavior to gain access to a website or server without having to overcome a security infrastructure. In this type of attack, hackers will try to trick an individual into just giving them the information they need.
Phishing is one of the best-known types of social engineering hacks. According to Google, effective phishing campaigns can have a 45 percent success rate.
Never hand over (or enter) passwords or personal information unless you are sure of the identity of the entity requesting it. Google, Facebook, banks and other institutions will never ask for this kind of information in an email. Also, do not click on suspicious links or use hardware you from a source you cannot identify. It is also a good idea to have published policies and training sessions to alert attorneys and staff about how to spot a social engineering attack.
In one baiting test, Steve Stasiukonis, VP and founder of Secure Network Technologies, Inc., placed 20 USB drives around the parking lot and public areas of one of Secure Network Technologies' clients. The drives contained a Trojan that would collect machine-specific information once plugged in. In the test, 15 employees picked up a drive and used it in a company computer.
This test was conducted in 2006, and methods of infection have only become more advanced.
5. Limit access to administrative accounts
If your firm uses WordPress, for example, limit the number of individuals at the firm with full administrative access. Reduce the number paths a hacker has to access your server, database or theme files. This will make it easier to keep your website secure, and it will make it easier to track the source of an infection and take steps to recover should a successful attack occur.
Google guides
As a part of its #NoHacked efforts, Google has created guides to help webmasters clean up websites that have been affected by three commonly known attacks. These include:
The gibberish hack guide: In a gibberish hack, the attacker will fill a page with meaningless content containing keywords relevant to your website. Then, when your page appears in search results for those terms and a searcher clicks on the listing, he or she will be redirected away from your site to the hacker's site.
The cloaked keywords hack guide: In a cloak attack, content and images are injected into a page that looks like it is part of the regular site. The content is usually hidden, so the pages appear benign.
The Japanese keyword hack guide: In this type of attack, hackers will set up pages full of Japanese text under random directories. Affiliate store links are placed on these pages that appear in Google results.
Google also provides advice for how to tell whether your site has been hacked and what steps you should take to recover from an infection. The best first steps are always prevention.

